Hello FWCloud,
First of all, thanks for your great work.
It would be great if FWCloud offered the same scripting options under System → Keepalived and other services like HA‑Proxy, etc., as it does in Policies (Input, Output, Forward).
With these options, you could generate all parameters of a configuration file via scripts and distribute them to all or individual nodes.
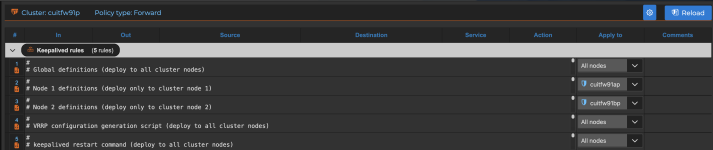
For this reason, I’ve put my Keepalived scripts into the Forward policy, where they obviously don’t belong.
The same would be cool under Routing as well.
Example
Script Line 1:
#
# Global definitions (deploy to all cluster nodes)
#
export VI_1_INTERFACE="eth0"
export VI_1_VIRTUAL_IPADDRESS_1="192.168.212.21"
export VI_1_ROUTER_ID="91"
export VI_1_AUTH_PASS="SECRET"
export VI_1_ADVERT_INT="1"
export VI_2_INTERFACE="eth1"
export VI_2_VIRTUAL_IPADDRESS_1="192.168.210.1"
export VI_2_ROUTER_ID="91"
export VI_2_AUTH_PASS="SECRET"
export VI_2_ADVERT_INT="1"
export VI_3_INTERFACE="eth2"
export VI_3_VIRTUAL_IPADDRESS_1="192.168.219.1"
export VI_3_ROUTER_ID="91"
export VI_3_AUTH_PASS="SECRET"
export VI_3_ADVERT_INT="1"
Script Line 2:
#
# Node 1 definitions (deploy only to cluster node 1)
#
export VI_1_STATE="MASTER"
export VI_1_PRIORITY="200"
export VI_2_STATE="MASTER"
export VI_2_PRIORITY="200"
export VI_3_STATE="MASTER"
export VI_3_PRIORITY="200"
Script Line 3:
#
# Node 2 definitions (deploy only to cluster node 2)
#
export VI_1_STATE="BACKUP"
export VI_1_PRIORITY="100"
export VI_2_STATE="BACKUP"
export VI_2_PRIORITY="100"
export VI_3_STATE="BACKUP"
export VI_3_PRIORITY="100"
Script Line 4:
#
# VRRP configuration generation script (deploy to all cluster nodes)
#
cat <<-EOF > /etc/keepalived/keepalived.conf.generated
! Configuration File for keepalived
global_defs {
router_id $HOSTNAME # Eindeutiger Name fuer diesen Keepalived-Knoten
}
!vrrp_script chk_httpd {
! script "/usr/bin/pgrep httpd" # Prueft, ob der Webserver laeuft
! interval 2 # Prueft alle 2 Sekunden
! weight 2 # Erhoeht die Prioritaet, wenn der Dienst laeuft
!}
vrrp_instance VI_1 {
state $VI_1_STATE # MASTER oder BACKUP
interface $VI_1_INTERFACE # Netzwerkinterface
virtual_router_id $VI_1_ROUTER_ID # ID des VRRP-Routers (255)
priority $VI_1_PRIORITY # Hoehere Zahl = hoehere Prioritaet
advert_int $VI_1_ADVERT_INT # Advertisement-Intervall (Sekunden)
authentication {
auth_type PASS # Authentifizierungstyp
auth_pass $VI_1_AUTH_PASS # Passwort (bis zu 8 Zeichen)
}
!track_script {
! chk_httpd # Fuegt das Skript hinzu
!}
virtual_ipaddress {
$VI_1_VIRTUAL_IPADDRESS_1 # Gemeinsame IP-Adresse (Floating IP)
}
}
vrrp_instance VI_2 {
state $VI_2_STATE # MASTER oder BACKUP
interface $VI_2_INTERFACE # Netzwerkinterface
virtual_router_id $VI_2_ROUTER_ID # ID des VRRP-Routers (255)
priority $VI_2_PRIORITY # Hoehere Zahl = hoehere Prioritaet
advert_int $VI_2_ADVERT_INT # Advertisement-Intervall (Sekunden)
authentication {
auth_type PASS # Authentifizierungstyp
auth_pass $VI_2_AUTH_PASS # Passwort (bis zu 8 Zeichen)
}
virtual_ipaddress {
$VI_2_VIRTUAL_IPADDRESS_1 # Gemeinsame IP-Adresse (Floating IP)
}
}
vrrp_instance VI_3 {
state $VI_3_STATE # MASTER oder BACKUP
interface $VI_3_INTERFACE # Netzwerkinterface
virtual_router_id $VI_3_ROUTER_ID # ID des VRRP-Routers (255)
priority $VI_3_PRIORITY # Hoehere Zahl = hoehere Prioritaet
advert_int $VI_3_ADVERT_INT # Advertisement-Intervall (Sekunden)
authentication {
auth_type PASS # Authentifizierungstyp
auth_pass $VI_3_AUTH_PASS # Passwort (bis zu 8 Zeichen)
}
virtual_ipaddress {
$VI_3_VIRTUAL_IPADDRESS_1 # Gemeinsame IP-Adresse (Floating IP)
}
}
EOF
Script Line 5:
#
# keepalived restart command (deploy to all cluster nodes)
#
echo ""
echo "**********************************"
echo "* KEEPALIVED CONFIGURATION CHECK *"
echo "**********************************"
keepalived -t && echo "PASS - Error code: $?" || echo "FAIL - Error code: $?"
echo ""
keepalived -t && service keepalived reload
First of all, thanks for your great work.
It would be great if FWCloud offered the same scripting options under System → Keepalived and other services like HA‑Proxy, etc., as it does in Policies (Input, Output, Forward).
With these options, you could generate all parameters of a configuration file via scripts and distribute them to all or individual nodes.
For this reason, I’ve put my Keepalived scripts into the Forward policy, where they obviously don’t belong.
The same would be cool under Routing as well.
Example
Script Line 1:
#
# Global definitions (deploy to all cluster nodes)
#
export VI_1_INTERFACE="eth0"
export VI_1_VIRTUAL_IPADDRESS_1="192.168.212.21"
export VI_1_ROUTER_ID="91"
export VI_1_AUTH_PASS="SECRET"
export VI_1_ADVERT_INT="1"
export VI_2_INTERFACE="eth1"
export VI_2_VIRTUAL_IPADDRESS_1="192.168.210.1"
export VI_2_ROUTER_ID="91"
export VI_2_AUTH_PASS="SECRET"
export VI_2_ADVERT_INT="1"
export VI_3_INTERFACE="eth2"
export VI_3_VIRTUAL_IPADDRESS_1="192.168.219.1"
export VI_3_ROUTER_ID="91"
export VI_3_AUTH_PASS="SECRET"
export VI_3_ADVERT_INT="1"
Script Line 2:
#
# Node 1 definitions (deploy only to cluster node 1)
#
export VI_1_STATE="MASTER"
export VI_1_PRIORITY="200"
export VI_2_STATE="MASTER"
export VI_2_PRIORITY="200"
export VI_3_STATE="MASTER"
export VI_3_PRIORITY="200"
Script Line 3:
#
# Node 2 definitions (deploy only to cluster node 2)
#
export VI_1_STATE="BACKUP"
export VI_1_PRIORITY="100"
export VI_2_STATE="BACKUP"
export VI_2_PRIORITY="100"
export VI_3_STATE="BACKUP"
export VI_3_PRIORITY="100"
Script Line 4:
#
# VRRP configuration generation script (deploy to all cluster nodes)
#
cat <<-EOF > /etc/keepalived/keepalived.conf.generated
! Configuration File for keepalived
global_defs {
router_id $HOSTNAME # Eindeutiger Name fuer diesen Keepalived-Knoten
}
!vrrp_script chk_httpd {
! script "/usr/bin/pgrep httpd" # Prueft, ob der Webserver laeuft
! interval 2 # Prueft alle 2 Sekunden
! weight 2 # Erhoeht die Prioritaet, wenn der Dienst laeuft
!}
vrrp_instance VI_1 {
state $VI_1_STATE # MASTER oder BACKUP
interface $VI_1_INTERFACE # Netzwerkinterface
virtual_router_id $VI_1_ROUTER_ID # ID des VRRP-Routers (255)
priority $VI_1_PRIORITY # Hoehere Zahl = hoehere Prioritaet
advert_int $VI_1_ADVERT_INT # Advertisement-Intervall (Sekunden)
authentication {
auth_type PASS # Authentifizierungstyp
auth_pass $VI_1_AUTH_PASS # Passwort (bis zu 8 Zeichen)
}
!track_script {
! chk_httpd # Fuegt das Skript hinzu
!}
virtual_ipaddress {
$VI_1_VIRTUAL_IPADDRESS_1 # Gemeinsame IP-Adresse (Floating IP)
}
}
vrrp_instance VI_2 {
state $VI_2_STATE # MASTER oder BACKUP
interface $VI_2_INTERFACE # Netzwerkinterface
virtual_router_id $VI_2_ROUTER_ID # ID des VRRP-Routers (255)
priority $VI_2_PRIORITY # Hoehere Zahl = hoehere Prioritaet
advert_int $VI_2_ADVERT_INT # Advertisement-Intervall (Sekunden)
authentication {
auth_type PASS # Authentifizierungstyp
auth_pass $VI_2_AUTH_PASS # Passwort (bis zu 8 Zeichen)
}
virtual_ipaddress {
$VI_2_VIRTUAL_IPADDRESS_1 # Gemeinsame IP-Adresse (Floating IP)
}
}
vrrp_instance VI_3 {
state $VI_3_STATE # MASTER oder BACKUP
interface $VI_3_INTERFACE # Netzwerkinterface
virtual_router_id $VI_3_ROUTER_ID # ID des VRRP-Routers (255)
priority $VI_3_PRIORITY # Hoehere Zahl = hoehere Prioritaet
advert_int $VI_3_ADVERT_INT # Advertisement-Intervall (Sekunden)
authentication {
auth_type PASS # Authentifizierungstyp
auth_pass $VI_3_AUTH_PASS # Passwort (bis zu 8 Zeichen)
}
virtual_ipaddress {
$VI_3_VIRTUAL_IPADDRESS_1 # Gemeinsame IP-Adresse (Floating IP)
}
}
EOF
Script Line 5:
#
# keepalived restart command (deploy to all cluster nodes)
#
echo ""
echo "**********************************"
echo "* KEEPALIVED CONFIGURATION CHECK *"
echo "**********************************"
keepalived -t && echo "PASS - Error code: $?" || echo "FAIL - Error code: $?"
echo ""
keepalived -t && service keepalived reload
Attachments
-
FWCloud Script.png (191.1 KB)
- File size
- 191.1 KB
- Download
- 2
-
Keepalived.png (59.2 KB)
- File size
- 59.2 KB
- Download
- 2