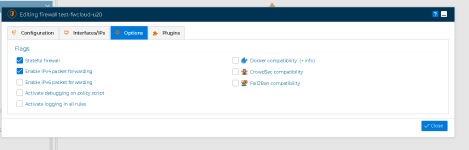
First - I have attached the "policy script" for your review. (see far bottom)
....................................................................................................................................
Second - Here is the configuration, which is just like your instructions (see below)
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
....................................................................................................................................
Third - Following your instructions. I should not be able to ping until the firewall is configured - see below
sysadmin@test-fwcloud-u20:~$ sudo docker exec -it lucid_nash /bin/bash root@46c7091f2789:/# ping -c 2 google.com
ping: google.com: Temporary failure in name resolution root@46c7091f2789:/# ping -c 2 google.com
ping: google.com: Temporary failure in name resolution
....................................................................................................................................
Forth - I'm not understanding how the "Translated Source" works or what it needs to be configured to.
Fifth - I am aware that the policy script log that's attach says echo "WARNING: IPTables not disabled in Docker configuration." I'm not sure if this is a error or just a notification.
...........................................................
....................................................................................................................................
Second - Here is the configuration, which is just like your instructions (see below)
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
....................................................................................................................................
Third - Following your instructions. I should not be able to ping until the firewall is configured - see below
sysadmin@test-fwcloud-u20:~$ sudo docker exec -it lucid_nash /bin/bash root@46c7091f2789:/# ping -c 2 google.com
ping: google.com: Temporary failure in name resolution root@46c7091f2789:/# ping -c 2 google.com
ping: google.com: Temporary failure in name resolution
....................................................................................................................................
Forth - I'm not understanding how the "Translated Source" works or what it needs to be configured to.
Fifth - I am aware that the policy script log that's attach says echo "WARNING: IPTables not disabled in Docker configuration." I'm not sure if this is a error or just a notification.
...........................................................