I've been testing applying a rule set to my server and re-importing it to see what happens. Here's a very simplified version of the rules that I applied:
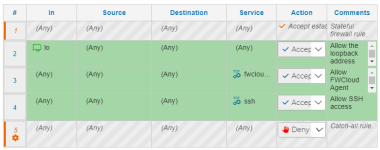
When I apply it and re-import it (using "iptables-save import"), my rules are changed to:
There's two issues that I'm seeing at play:
Here's the iptables export without the logging jump chain for the Catch-All rule. This will allow an import without the duplicated Catch-All, but also without logging:
Thanks,
Jeremy

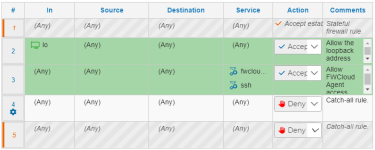
When I apply it and re-import it (using "iptables-save import"), my rules are changed to:

There's two issues that I'm seeing at play:
- If a rule has the same Source and Destination, but different Services, they are merged into a single row. Even if there's a unique comment on each item.
- If you enable logging on the default Catch-All rule, it changes the jump target from DROP to a :FWCRULE####.LOG chain. The import function isn't able to recognize that this is a Catch-All jump chain and update the logging flag on the new rule. Instead it inserts it as an additional rule.
*filter
:INPUT DROP [0:0]
:FORWARD DROP [0:0]
:OUTPUT DROP [0:0]
:FWCRULE136.LOG - [0:0]
-A INPUT -m comment --comment "Stateful firewall rule." -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A INPUT -i lo -m comment --comment "{\"fwc_rs\":\"#A5D6A7\"}Allow the loopback address access to anything." -m conntrack --ctstate NEW -j ACCEPT
-A INPUT -p tcp -m comment --comment "{\"fwc_rs\":\"#A5D6A7\"}Allow FWCloud Agent access" -m tcp --dport 33033 -m conntrack --ctstate NEW -j ACCEPT
-A INPUT -p tcp -m comment --comment "{\"fwc_rs\":\"#A5D6A7\"}Allow SSH access" -m tcp --dport 22 -m conntrack --ctstate NEW -j ACCEPT
-A INPUT -m comment --comment "Catch-all rule." -j FWCRULE136.LOG
-A FORWARD -m comment --comment "Stateful firewall rule." -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A FORWARD -m comment --comment "Catch-all rule." -j DROP
-A OUTPUT -m comment --comment "Stateful firewall rule." -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A OUTPUT -m comment --comment "Catch-all rule." -j ACCEPT
-A FWCRULE136.LOG -m limit --limit 1/sec -j LOG --log-prefix "RULE ID 136 [DROP] " --log-level 6
-A FWCRULE136.LOG -j DROP
COMMIT
Here's the iptables export without the logging jump chain for the Catch-All rule. This will allow an import without the duplicated Catch-All, but also without logging:
*filter
:INPUT DROP [0:0]
:FORWARD DROP [0:0]
:OUTPUT DROP [0:0]
-A INPUT -m comment --comment "Stateful firewall rule." -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A INPUT -i lo -m comment --comment "{\"fwc_rs\":\"#A5D6A7\"}Allow the loopback address access to anything." -m conntrack --ctstate NEW -j ACCEPT
-A INPUT -p tcp -m comment --comment "{\"fwc_rs\":\"#A5D6A7\"}Allow FWCloud Agent access" -m tcp --dport 33033 -m conntrack --ctstate NEW -j ACCEPT
-A INPUT -p tcp -m comment --comment "{\"fwc_rs\":\"#A5D6A7\"}Allow SSH access" -m tcp --dport 22 -m conntrack --ctstate NEW -j ACCEPT
-A INPUT -m comment --comment "Catch-all rule." -j DROP
-A FORWARD -m comment --comment "Stateful firewall rule." -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A FORWARD -m comment --comment "Catch-all rule." -j DROP
-A OUTPUT -m comment --comment "Stateful firewall rule." -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A OUTPUT -m comment --comment "Catch-all rule." -j ACCEPT
COMMIT
Thanks,
Jeremy
