Hi
I'm facing a strange issue with the firewall rule.
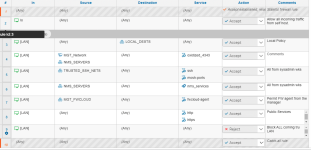
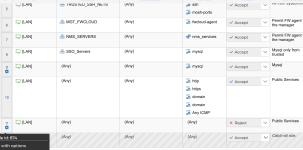
I've basically create a simple host firewall rule in wich:
1) i filter ONLY inbound traffic on the lan interface (labeled: LAN) - INPUT CHAIN
2) i let all permitted outgoing - OUTPUT CHAIN
3) i deny all in the FORWARD CHAIN
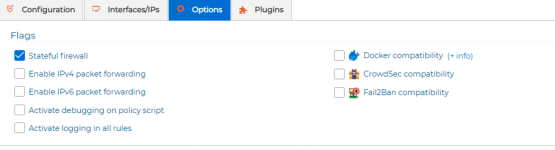
4) firewall type: iptables.
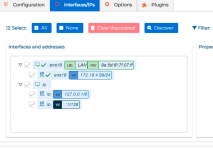
attached are the screenshot of the configuration .
As you can see nothing fancy: just a bunch of rules to permit/deny.
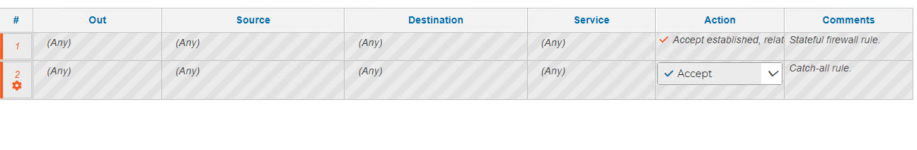
The catchall rules is set on PERMIT.
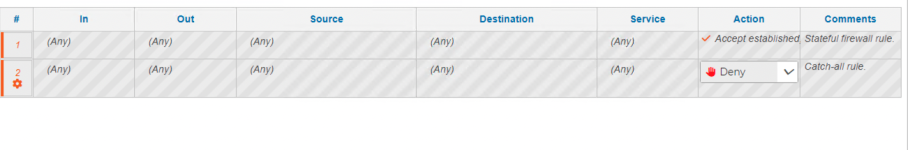
I've added rule:9 as catchall deny rule for interface labelled lan.
What i'm expecting is that the rule 9 (id 58) is triggered only for traffic that not match the rule above it.
What happens instead is that i've receive log like that:
[2047966.859210] RULE ID 58 [REJECT] IN=ens18 OUT= MAC=9a:5d:6f:7f:07:ff:9a:56:1a:6a:9d:4a:08:00 SRC=10.0.2.102 DST=172.18.4.99 LEN=60 TOS=0x00 PREC=0x00 TTL=63 ID=0 DF PROTO=TCP SPT=3306 DPT=53398 WINDOW=65160 RES=0x00 ACK SYN URGP=0
where: dst=172.18.4.99 is the host's firewall ip ens18 (LAN) and the src is another host in lan.
The interesting point in that is the spt=3306, wich is a mysql port.
So basically this is a returning traffic for a connection that host firewall (172.18.4.99) makes to 10.0.2.102 on port 3306 (so: OUTPUT chain).
But why this kind of traffic (outbound) is matched by rule 9/id:58 ? normally the returning traffic should be managed by the stateful feature of the firewall.
Am i Missing something ?
Thx n advance.
I'm facing a strange issue with the firewall rule.
I've basically create a simple host firewall rule in wich:
1) i filter ONLY inbound traffic on the lan interface (labeled: LAN) - INPUT CHAIN
2) i let all permitted outgoing - OUTPUT CHAIN
3) i deny all in the FORWARD CHAIN
4) firewall type: iptables.
attached are the screenshot of the configuration .
As you can see nothing fancy: just a bunch of rules to permit/deny.
The catchall rules is set on PERMIT.
I've added rule:9 as catchall deny rule for interface labelled lan.
What i'm expecting is that the rule 9 (id 58) is triggered only for traffic that not match the rule above it.
What happens instead is that i've receive log like that:
[2047966.859210] RULE ID 58 [REJECT] IN=ens18 OUT= MAC=9a:5d:6f:7f:07:ff:9a:56:1a:6a:9d:4a:08:00 SRC=10.0.2.102 DST=172.18.4.99 LEN=60 TOS=0x00 PREC=0x00 TTL=63 ID=0 DF PROTO=TCP SPT=3306 DPT=53398 WINDOW=65160 RES=0x00 ACK SYN URGP=0
where: dst=172.18.4.99 is the host's firewall ip ens18 (LAN) and the src is another host in lan.
The interesting point in that is the spt=3306, wich is a mysql port.
So basically this is a returning traffic for a connection that host firewall (172.18.4.99) makes to 10.0.2.102 on port 3306 (so: OUTPUT chain).
But why this kind of traffic (outbound) is matched by rule 9/id:58 ? normally the returning traffic should be managed by the stateful feature of the firewall.
Am i Missing something ?
Thx n advance.
Attachments
-
Screenshot 2023-01-03 at 09.45.08.png (476.4 KB)
- File size
- 476.4 KB
- Download
- 2
-
Screenshot 2023-01-03 at 09.45.24.png (226.1 KB)
- File size
- 226.1 KB
- Download
- 2
-
Screenshot 2023-01-03 at 09.45.32.png (226.8 KB)
- File size
- 226.8 KB
- Download
- 1
-
Screenshot 2023-01-03 at 09.45.51.png (138.3 KB)
- File size
- 138.3 KB
- Download
- 1
-
Screenshot 2023-01-03 at 09.45.59.png (175.6 KB)
- File size
- 175.6 KB
- Download
- 2
Last edited: